Importance of Physical Security in Cybersecurity
I had a lecture on physical security at my university last semester which completely changed how I look at physical security.
We spend so much time worrying about firewalls, encryption, zero-day exploits and multi-factor authentication. Meanwhile, there is probably an unlocked window in your office building right now that someone could open with a credit card.
Let us together rethink the concepts of physical security and how it is often overlooked in the cybersecurity industry.
Key Boxes Are a Joke
You know those key lockboxes outside buildings? Or if you live near me, on a tree? The ones elder care agencies use, or maintenance companies, or Airbnb hosts? The ones that are supposed to keep a spare key secure?

They’re basically a small metal box with a combination lock. You put the key inside, set a code, and then anyone with the code can open it and get the key.
Most of them use a 4-digit combination. That’s 10,000 possible codes. Sounds like a lot until you realize that:
- People use obvious codes like 1234, 0000, or the street address
- The buttons get worn down from use, so you can see which numbers are in the code
- You can feel or hear the mechanism click when you get a digit right
Or you could simply just take a hammer to it and break it open in seconds. The locks on these things are so cheap and flimsy that they don’t even provide a real barrier. In fact, some models can be opened with a piece of paper or a soda can. You just slide it in, wiggle it around, and the lock pops open.
Companies spend thousands on access control systems for the front door, then stick a $30 lockbox with the master key on the side of the building.
Metal Doors With Giant Obvious Weaknesses
Fire doors. Security doors. Those heavy metal doors with the “push bar” on the inside that are supposed to keep people out.

Here’s the thing about a lot of them, if you manage to pierce the doors from one side to the other, you can simply use a long piece of metal to push down the crash bar mechanism from the outside.
Windows and Doors You Can Just… Remove
A lot of windows and doors are held in place by pins or screws that are accessible from the outside. Especially older buildings, or places where they prioritized making maintenance easy.
You don’t need to break the glass. You don’t need to pick any locks. You just unscrew a few things, and the whole window pops out. Or the door comes off its hinges.
Our lecturer even told us how he performed a physical pentest on a building where he found a window that was held in place by screws that were accessible from the outside. He unscrewed them, took the window out, and walked right in. Nobody asked any questions because it looked like a maintenance issue.
Lockpicking Is Easier Than You Think
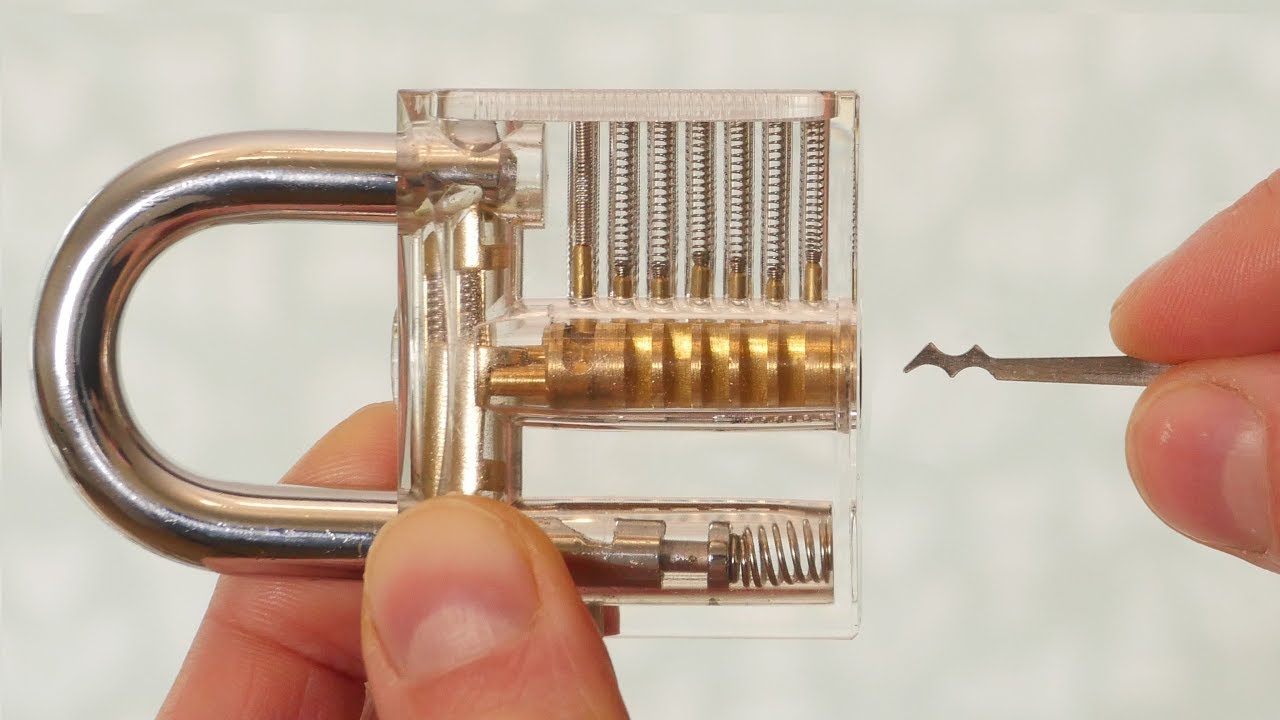
Lockpicking is way easier than movies make it look. Not the crazy picking while hanging from a ceiling kind. But the “I watched a YouTube video and practiced for an hour” kind.
Most commercial door locks are pin tumbler locks. The same basic design that’s been around for many years. And most of them can be picked by someone with basic tools and minimal practice.
But honestly, why bother picking locks when there are easier ways?
Rake picks. Literally just jiggle this thing in the lock for a few seconds and some locks will pop open.
Or you could try the bump key method. A specially cut key that you insert and then strike with a hammer. The force causes the pins to jump, allowing you to turn the lock. It’s like a one-size-fits-all master key for pin tumbler locks.
Or just use the oldest trick in the book: tailgating. Walk confidently behind someone who has legitimate access. Carry a box or a coffee. Look like you belong. 90% of the time, people will hold the door for you because they don’t want to be rude.
Key-alike Systems Are a Nightmare
Some buildings use key-alike systems where multiple doors are opened by the same key. It sounds convenient, but it creates a huge security risk. If someone gets a copy of that one key, they can access every door in the building that uses it.
An example of this is TSA master keys. They are used to open luggage locks at airports. But there are only a few different master keys, and they can be easily found online. If someone gets one of those keys, they can open any luggage that uses those locks.
Camera Weaknesses
Every building has cameras now. Hallways, entrances, parking lots, loading docks. Tons of cameras recording everything 24/7.

They are most likely not monitored in real time. The cameras are recording to a DVR or cloud storage somewhere. Security guards might glance at a monitor occasionally. But unless an alarm goes off, nobody’s really paying attention to the feeds in real time.
Which means cameras are great for figuring out what happened after something goes wrong, but pretty terrible at preventing things from happening in the first place.
And even then, there are issues:
Blind spots. Every camera system has them. Corners where the angle doesn’t quite reach. Areas blocked by furniture or equipment. Figure out the blind spots and you can move around mostly invisible.
Camera quality. A lot of older systems have terrible resolution. You can see that someone was there, but you can’t identify them unless they stare directly at the camera for a while.
Storage limits. Many systems only keep footage for 7-30 days before overwriting it. So if nobody notices something was wrong until a month later, the footage is gone.
Physical access to the cameras. If you can reach the camera, you can disable it. Spray paint on the lens, unplug the cable or point it at the ceiling.
Detecting Infrared cameras. Some cameras have infrared sensors for night vision. You can use an your phone camera, as most phone cameras can see infrared light. If you point your phone at a camera and see a bright light, it’s probably an IR camera.

Basicly, cameras are a great tool for investigation and deterrence, but they shouldn’t be your only line of defense. If someone is determined to get in, they can find ways to avoid or disable the cameras.
The Printer Room Backdoor
This is the one that really got me.

Most office buildings have printer rooms or supply closets scattered around each floor. And in those rooms? Ethernet cables. Connected directly to the corporate network.
Here’s the attack:
- Walk into the building (tailgate, use the key from the lockbox, pick the lock, whatever)
- Find a printer room or supply closet
- Plug in a tiny device (Raspberry Pi, throwaway laptop, whatever)
- Walk out
That device is now on the internal network. Behind the firewall. Behind all the perimeter security. It can scan for other devices, try to access file shares, attempt to escalate privileges, phone home to an external server.
All because someone left an ethernet port accessible in an unlocked room.
Even server rooms can have this issue. If the door is unlocked, or if there’s a maintenance hatch, or if the access control system is weak, an attacker can get in and plug in a device directly to the network and extract data or cause damage.
Badge Cloning Is Easier Than You Think
RFID badges are super common for access control. Tap your badge, door unlocks, and you walk in.

Except a lot of these systems use older RFID technology that can be cloned trivially. You can buy an RFID reader/writer on Amazon for almost no money. Get close enough to someone’s badge for a second or two, and you can copy it.
Then you have your own badge with the same credentials as the person you cloned it from.
Here some high-value targets for badge cloning could be cleaning staff, contractors, or anyone who has access to secure areas but might not be subject to the same background checks as full-time employees. If an attacker can clone a badge from someone like that, they can get into areas that are supposed to be off-limits.
Access Control Systems Are Often Insecure
Access control systems are intended to keep unauthorized people out, but in practice, many have significant vulnerabilities due to outdated technology or poor security implementation. One example i the Wiegand protocol, it’s still used in a huge number of systems, but it doesn’t offer any encryption and is easy to spoof. Older RFID-based systems also have major weaknesses, as many can be cloned with cheap hardware.

Newer protocols like OSDP V2 represent a significant improvement, with support for encryption and mutual authentication, but unfortunately, adoption across the industry is still low. That means many companies are still relying on legacy systems that can be bypassed with surprisingly basic attacks.
Mifare Classic cards, which are still widely used, are particularly vulnerable. They can be cloned with a simple reader/writer that costs around $20. This means that if an attacker can get close enough to someone’s badge, they can easily create a copy and gain unauthorized access.
ESPKey devices, which are small and portable, can intercept or inject Wiegand signals, making it even easier for attackers to bypass access control systems that rely on this protocol.
So while access control systems are a critical component of physical security, many of them have vulnerabilities that can be exploited with relatively simple tools and techniques.
Air Gaps
“Air gapped” systems are supposed to be completely isolated from networks. No internet connection, no wifi, no way to access them remotely.
Sounds secure until you remember that:
- USB drives exist and people use them
- Bluetooth exists and has a range of about 10 meters
- People take smartphones into supposedly secure areas
- Cleaning staff have physical access
- Contractors come and go
If someone can get physical access to an air-gapped system, they can install malware via USB, extract data to a phone over Bluetooth, photograph screens, whatever.
The famous Stuxnet attack on Iranian nuclear facilities targeted air-gapped systems. The malware got in via USB drives, probably through an insider or through social engineering.
Critical Infrastructure Is Especially Vulnerable
Power plants, water treatment facilities, transportation systems. These are often considered critical infrastructure and are supposed to be highly secure. But they can have the same physical security weaknesses as any other building.

In fact, they can be even more vulnerable because they often have legacy systems, less frequent security audits, and a higher tolerance for physical access due to maintenance needs.
Even a single successful physical breach in a critical infrastructure facility can have devastating consequences, from power outages to water contamination to transportation disruptions.
And substations, which are crucial for power distribution, can take years to replace if damaged. The shortage of key components, like transformers due to the Ukraine/Russia war, makes them an attractive target for attackers.
Why This Matters
Here’s the thing that really stuck with me from that lecture:
We’ve built this whole massive cybersecurity industry focused on digital threats. And yeah, those are real and important. But we’ve created this weird blind spot where people think that if the network is secure, they’re safe.
The best firewall in the world doesn’t matter if someone can walk into your building, plug a device into an unsecured network port, and have full internal access.
And it happens. Pentesting companies get into corporate buildings all the time using these techniques. They don’t need to hack anything. They just need to look confident, wear a vest, and walk in through a door someone left open.
